Since HTTP/2 is supported in Firefox 36 and there is a partially functional http2 dissector in Wireshark I thought I’d take a look at what HTTP/2 packets look like in Wireshark. I’m using Kali where I needed to grab the following;
- Wireshark dev – 1.99.2
- Firefox 36
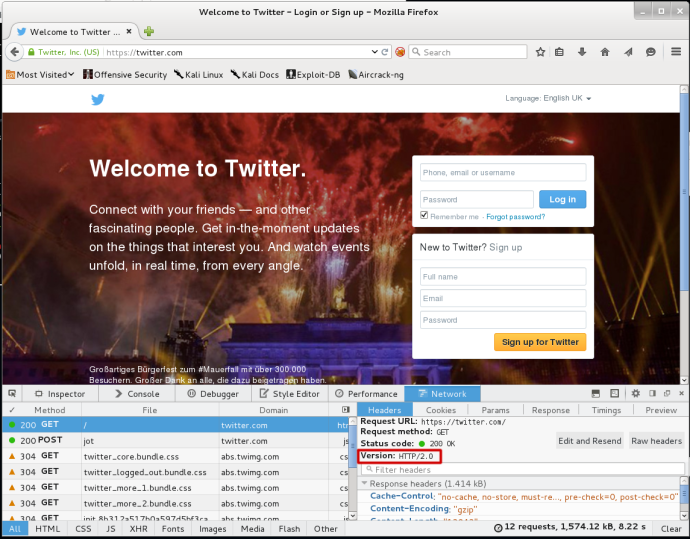
Firefox 36 by default uses TLS 1.2 when communicating over HTTP/2 you can view HTTP/2 traffic in the ‘Network’ tab in Firefox’s developer tools (f12).
To see these packets in Wireshark you need to point Wireshark at the SSLKEYLOGFILE that is written by NSS. This enables you to see the http2 packets and decrypt any encrypted data over SSL, TLS etc. Here’s a quick set up to get that up and running;
Wireshark
wget https://1.eu.dl.wireshark.org/src/wireshark-1.99.2.tar.bz2 -O /opt/tar -jxf wireshark-1.99.2.tar.bz2
Install dependencies
apt-get install libpcap-dev
Configure and install
cd wireshark-1.99.2./configure --with-gtk2make && make install
Edit /etc/ld.so.conf
Add the line >
include /usr/local/lib
Then run the command ldconfig
Run Wireshark > ./wireshark
Firefox
wget firefox -O /opttar -jxf firefox-36.0.tar.bz2
Make a file on the file system and set an environment variable enabling NSS to write key logs so that Wireshark can decrypt any TLS traffic.
mkdir ~/tls && touch ~/tls/sslkeylog.logexport SSLKEYLOGFILE=~/tls/sslkeylog.log
Run Firefox (within the same terminal you set the environment variable or add the env. variable to your .bashrc) > ./firefox
Wireshark
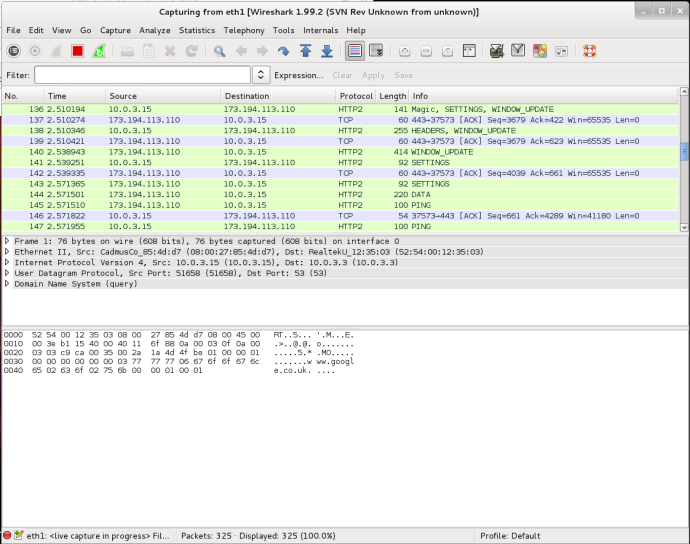
Point Wireshark to the sslkeylog.log so that it can decrypt TLS traffic.
- Edit -> Preferences -> Protocols -> SSL
- (Pre)-Master-Secret log filename -> /root/tls/sslkeylog.log
Start a new live capture in Wireshark and in Firefox navigate to an HTTP/2 enabled website e.g. https://twitter.com and view the HTTP/2 packets.
References: